Decentralized Identity
Definitions
Digital identity is the sum of all the (digital) information that exists about you. For example:
- core identity attributes (name, address or birthday),
- education and work history (diplomas, work records, certificates),
- health or insurance data (medical reports, prescriptions, vaccination passes),
- financial information (bank account information, transaction histories).
As a result, your digital identity describes who you are in every aspect of your (digital) life.
Decentralized identity is simply one (of many) approaches for making digital identity possible.
How decentralized identity works
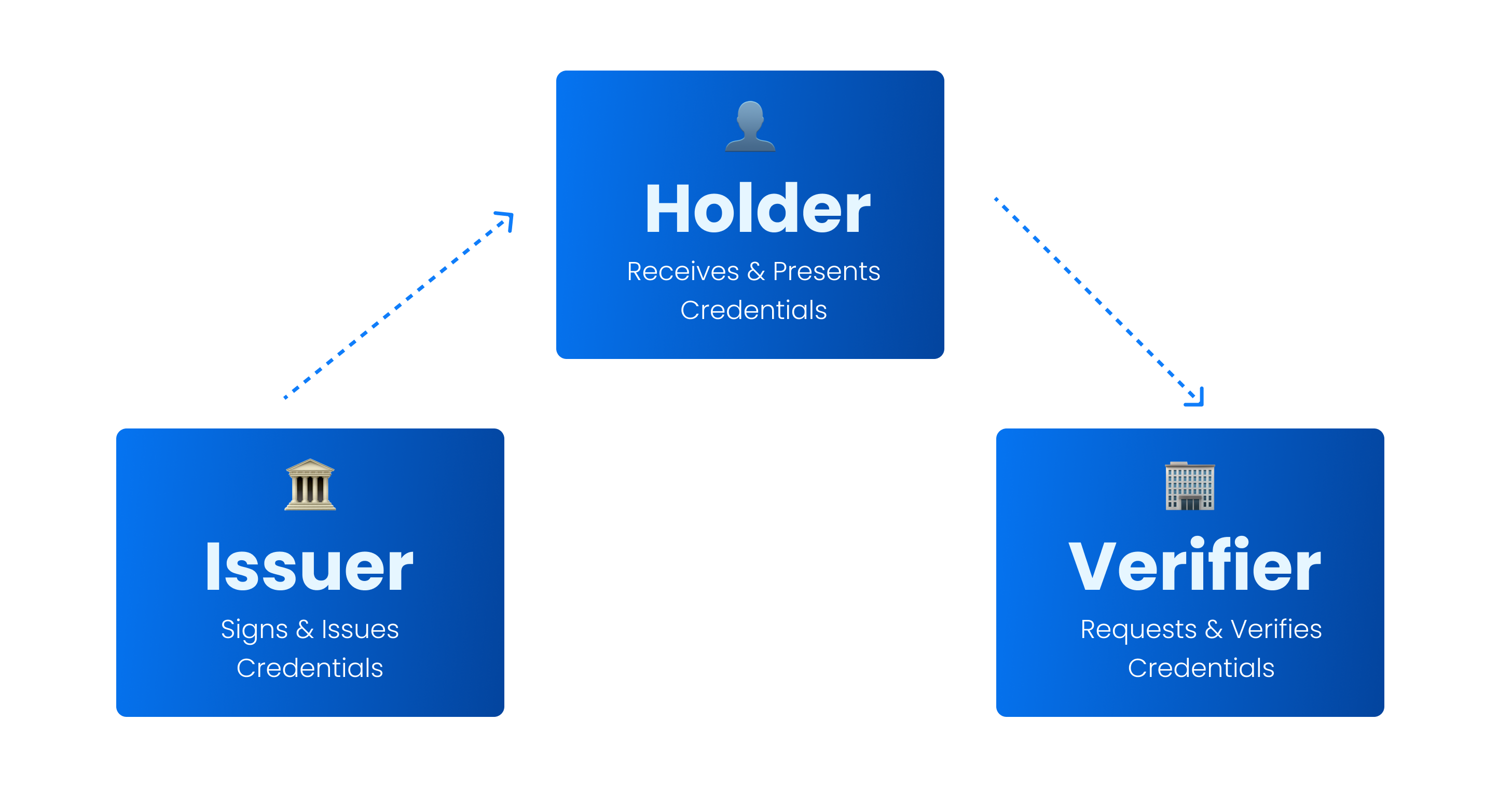
Decentralized identity enables governments and businesses to issue identity credentials to their citizens, users or other stakeholders. These credentials are stored in ID wallets and can be easily shared with others. It is like a 3-sided marketplace:
- Issuers issue digital identity credentials (e.g. governments issue passports, universities issue diplomas).
- Holders receive digital credentials (from Issuers) and store them in ID wallets. They control and share their digital credentials with third parties (Verifiers).
- Verifiers rely on identity data to provide products and services, they verify and process credentials provided by Holders.
The so-called “Trust Triangle” illustrates these roles:
Technology & Building Blocks
Decentralized identity is based on a set of complex technologies and protocols which can be thought of as building blocks that are available in different variations and can be put together in different ways. As a result, there are different “flavors” or ways to implement decentralized identity depending on the business requirements.
The following list outlines some of the most important ones:
- Cryptographic keys convey control over digital identities and enable core functionality such as encryption and authentication.
- Decentralized Identifiers (DIDs, W3C) establish a public key infrastructure by linking keys to identifiers allowing parties to find and interact with each other.
- Digital Credentials like Verifiable Credentials (VCs, W3C) and mobile driver’s license/mdoc (ISO/IEC 18013-5/-7) are the most common “types” of digital credentials. They can be easily and securely shared with and verified by others. (Note that they are never stored on a blockchain due to privacy and compliance reasons.)
- Selective Disclosure (SD) and Zero Knowledge Proofs (ZKPs) are ways to minimize data exposure. Selective disclosure using SD-JWTs (IETF) is a solid and reliable way to improve users’ privacy that is gaining traction. While ZKPs are a promising technology with a bright future, they are not yet broadly adopted due to concerns or lacking certifications of the underlying cryptography,
- Non-Fungible Tokens (NFTs) and Soulbound Tokens (SBTs) are used to tokenize proofs or assets on blockchains. They enable “ownership-based access” such as for holders of tickets or memberships. Also, they enable on-chain proofs that can be processed by smart contracts (without the use of oracles).
- Data Exchange Protocols enable the transfer of identity credentials between parties (like Issuer to Holder or Holder to Verifier). Currently, OpenID Connect, the standard that already enables federated identity, is evolving into the most used standard for the exchange of digital credentials. Protocols can enable data exchange online and in-person scenarios (even offline).
- ID Wallets store our keys (control) and credentials (identity data). They enable the management and sharing of our identity data via easy-to-use apps.
Walt.id
We’re building open source decentralized identity and wallet infrastructure trusted by thousands of developers, governments and businesses. Our goal is to enable anyone to build use cases and applications based on decentralized identity fast and with ease.
Our infrastructure enables organizations to become Issuers, Wallet Providers and Verifiers.
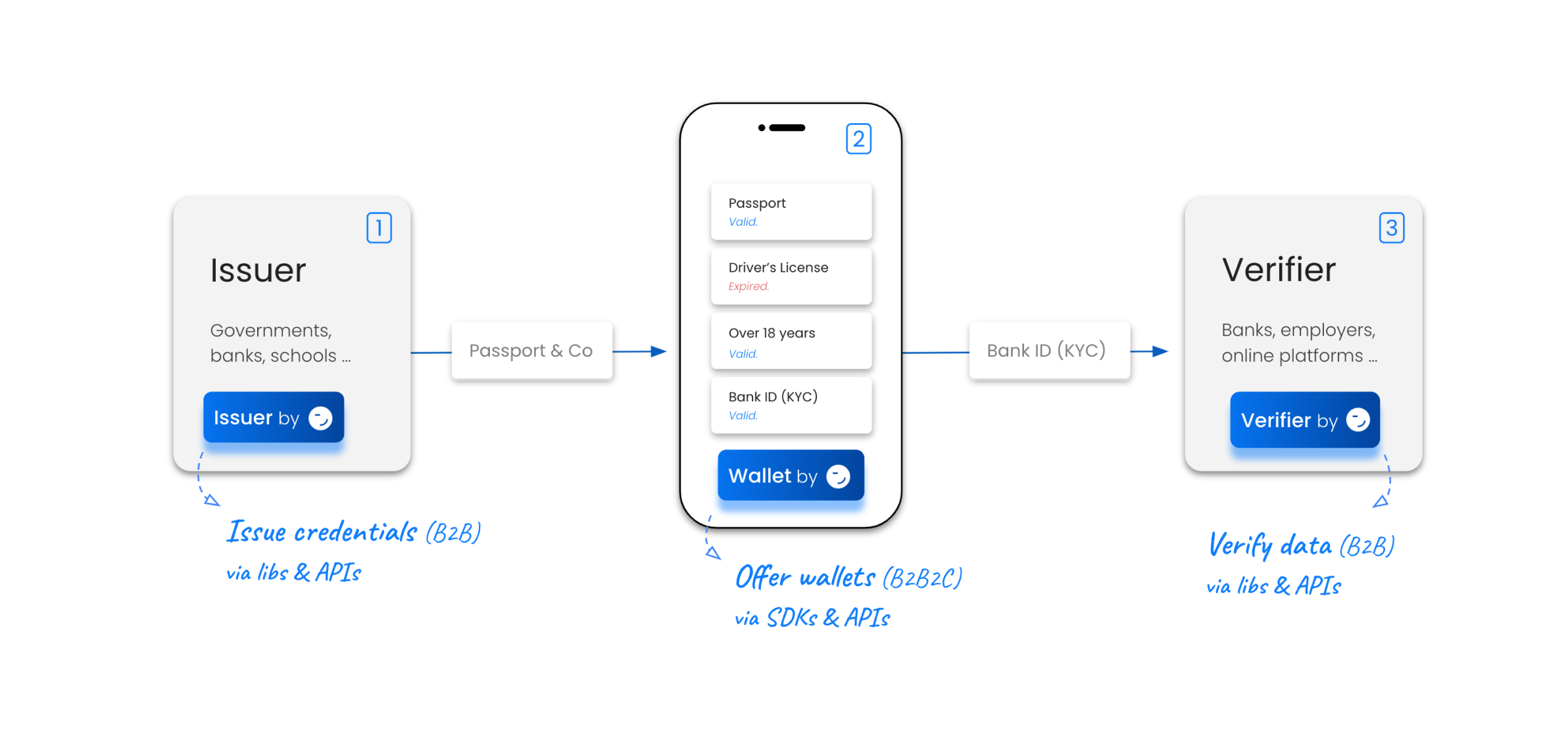
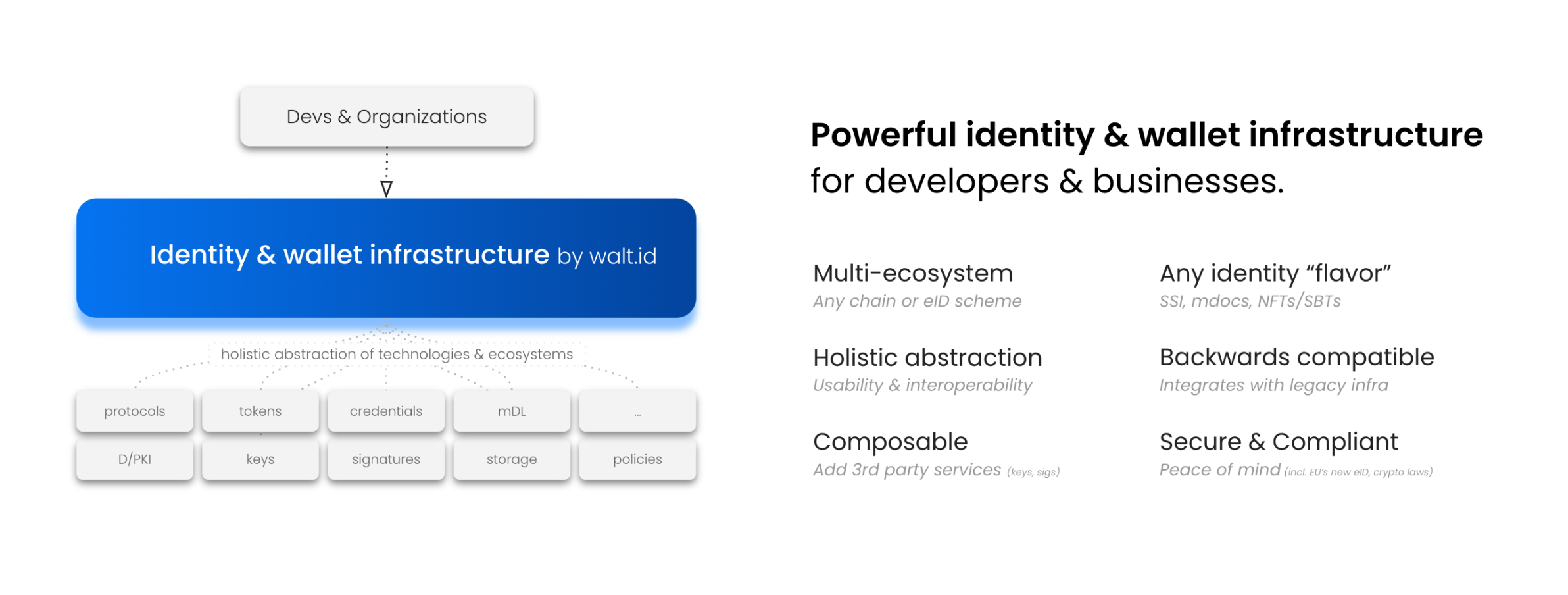
You can think of our infrastructure as an abstraction layer that hides technical complexity and handles different building blocks (e.g., trust registries, credential types, data exchange protocols) while ensuring ongoing compliance with standards and regulations.
Further Readings
You can learn more about decentralized identity in our ebooks:
- Decentralized Identity Playbook (eBook)
- Introduction to Digital Identity (eBook)
- Introduction to Decentralized Identity / Self-Sovereign Identity (eBook)
- Introduction to non-fungible (NFTs) and soulbound tokens (SBTs) for identity (eBook)
- NFTs/SBTs vs Self-Sovereign Identity (eBook)
- Monetizing decentralized identity (eBook)
- The rise of identity ecosystems (eBook)
- The role of blockchain for decentralized identity (eBook)
- eIDAS2 is here (eBook in collaboration with Trustscape)
- Me, myself and SSI (eBook in collaboration with BCG)
- A digital twin for everything (eBook in collaboration with BCG)
- Introduction to Digital Identity (eBook)
- Introduction to Decentralized Identity / Self-Sovereign Identity (eBook)
- Introduction to non-fungible (NFTs) and soulbound tokens (SBTs) for identity (eBook)
- NFTs/SBTs vs Self-Sovereign Identity (eBook)
- Monetizing decentralized identity (eBook)
- The rise of identity ecosystems (eBook)
- The role of blockchain for decentralized identity (eBook)
- eIDAS2 is here (eBook in collaboration with Trustscape)
- Me, myself and SSI (eBook in collaboration with BCG)
- A digital twin for everything (eBook in collaboration with BCG)
