AWS REST API
The issuer API can leverage AWS key management service to hook into the "cryptography as a service" or "encryption as a service" features provided by AWS. With that, the issuer API can sign and verify credentials whilst keeping the secrets (signing keys) in an external secure environment.
If you are new to AWS kms make sure to check out the guides here. The rest of this document assumes you already know how AWS KMS works, and you have it setup.
Method : Using AWS access keys and secret keys
Prerequisites
- AWS Account: You need an active AWS account. If you don't have one, create it at AWS Console.
Create AWS Access Keys and Secret Keys
To securely interact with AWS services such as KMS, you need to configure your AWS access and secret keys. Here’s how to generate and configure these credentials:
- Log in to your AWS Management Console.
- Navigate to IAM (Identity and Access Management).
- In the left sidebar, click on Users, then choose your username.
- Go to the Security credentials tab.
- Under Access keys, click Create access key.
- Copy both the Access Key ID and Secret Access Key. Store them securely.
Key generation
To create the key you can use the onboard endpoint provided by the issuer API and provide the necessary parameters to create the key in the AWS KMS service.
Creation via Issuer API
Endpoint:/onboard/issuer | API Reference
Example Request
curl -X 'POST' \
'https://issuer.portal.walt-test.cloud/onboard/issuer' \
-H 'accept: application/json' \
-H 'Content-Type: application/json' \
-d '{
"key": {
"backend": "aws-rest-api",
"keyType": "secp256r1",
"config": {
"auth": {
"accessKeyId": "AKIAW......U2TQU5F",
"secretAccessKey": "6YDrEN1t+......I3OCwSc7Sr",
"region": "eu-central-1"
}
}
},
"did": {
"method": "jwk"
}
}'
Body
{
"key": {
"backend": "aws-rest-api",
"keyType": "secp256r1",
"config": {
"auth": {
"accessKeyId": "AKIAW......U2TQU5F",
"secretAccessKey": "6YDrEN1t+......I3OCwSc7Sr",
"region": "eu-central-1"
}
}
},
"did": {
"method": "jwk"
}
}
Body Parameters
keybackend: String - Specifies the storage type of key. It can bejwk(manged by you),aws-rest-api(managed by AWS KMS using Rest api requests ) and others. Learn more about different types here.keyType: String - the algorithm used to generate the key. For Vault only ed25519 is possible.configaccessKeyId: String - The access key id for AWS KMS.secretAccessKey: String - The secret access key for AWS KMS.region: String - The region where the AWS KMS service is located.
did:method: String - Specifies the DID method. It can be key, jwk, web, cheqd.
Key Usage
Once you have successfully created a key that is one of the supported types listed above, you can use it in sign and issue operations offered by the issuer API.
If you've already had a look at
our /sign, /issue, /batchIssue
endpoints, you have seen that they all follow a similar request body structure, where the key that should be
used for signing credentials is provided via the issuerKey property. Now instead of providing the key as JWK, we
provide
a reference to a key stored in Vault with the required parameters and access credentials.
Below you can see an example of
issuerKey object referencing a key stored in AWS.
{
"issuerKey": {
"type": "aws-rest-api",
"config": {
"auth": {
"accessKeyId": "AKIAW......U2TQU5F",
"secretAccessKey": "6YDrEN1t+......I3OCwSc7Sr",
"region": "eu-central-1"
}
},
"id": "324ebf67-6bcc-4439-8b81-260bf0a82532",
"_publicKey": "{\"kty\":\"EC\",\"crv\":\"P-256\",\"x\":\"RfvJGDXOjz3NOSKgZ0VlijXST8S-j96DrG0C1AMNAK8\",\"y\":\"vSt2q7yIy0-AhAirMuuDmUScxkgf4JVfId-vTETraQA\"}",
"_keyType": "secp256r1"
},
"issuerDid": "did:jwk:eyJrdHkiOiJFQyIsImNydiI6IlAtMjU2IiwieCI6IlJmdkpHRFhPanozTk9TS2daMFZsaWpYU1Q4Uy1qOTZEckcwQzFBTU5BSzgiLCJ5IjoidlN0MnE3eUl5MC1BaEFpck11dURtVVNjeGtnZjRKVmZJZC12VEVUcmFRQSJ9"
}
Properties
type: String - the type of key can be either "aws" when using AWS KMS or "jwk" when providing the key in full as JWK.id: String - the ID of the key in the Transit Engine.configaccessKeyId: String - The access key id for AWS KMS.secretAccessKey: String - The secret access key for AWS KMS.region: String - The region where the AWS KMS service is located.
_publicKey(optional): Array - The public key can be fetched by the issuer API or directly provided, saving resources and reducing network requests._keyType(optional): String - The key type can be fetched by the issuer API or directly provided, saving resources and reducing network requests. ::
Method : Instance Authentication
Prerequisites
- AWS Account: You need an active AWS account. If you don't have one, create it at AWS Console.
Set Up an IAM Role for the EC2 Instance
To authenticate your instance with AWS, You can Set Up an IAM Role for the EC2 Instance in AWS Console by following the steps below:
- Log in to your AWS Management Console.
- Navigate to IAM (Identity and Access Management).
- In the left sidebar, click on Roles.
- Click on Create Role.
- Select EC2 as the service that will use this role.
- Click on Next: Permissions.
- Attach the necessary permissions to the role.
- Click on Next: Tags.
- Add tags if necessary.
- Click on Next: Review.
- Enter a name for the role.
- Click on Create Role.
- Attach the role to the EC2 instance.
- Navigate to the EC2 instance in the AWS Management Console.
- Click on Actions > Security > Modify IAM Role.
- Select the role you created.
- Click on Save.
- The EC2 instance is now authenticated with AWS.
- You can now use the AWS SDK to interact with AWS services.
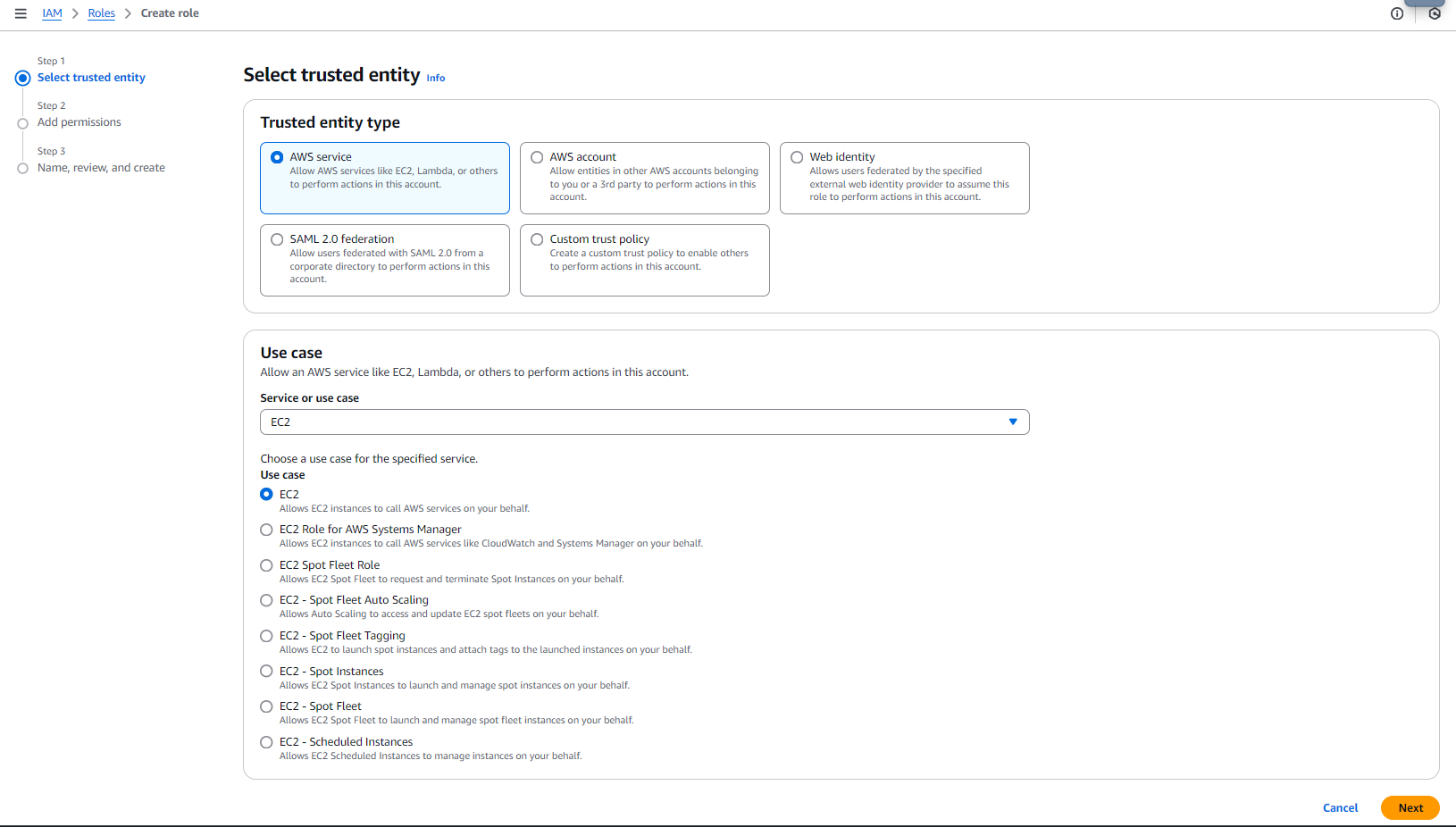
When you have set up the IAM role for the EC2 instance, you can use it to authenticate with AWS services.
Key generation
To create the key you can use the onboard endpoint provided by the issuer API and provide the necessary parameters to create the key in the AWS KMS service.
Creation via Issuer API
Endpoint:/onboard/issuer | API Reference
Example Request
curl -X 'POST' \
'https://issuer.portal.walt-test.cloud/onboard/issuer' \
-H 'accept: application/json' \
-H 'Content-Type: application/json' \
-d '{
"key": {
"backend": "aws-rest-api",
"keyType": "secp256r1",
"config": {
"auth": {
"roleName": "AccessRole",
"region": "eu-central-1"
}
},
},
"did": {
"method": "jwk"
}
}'
Body
{
"key": {
"backend": "aws-rest-api",
"keyType": "secp256r1",
"config": {
"auth": {
"roleName": "AccessRole",
"region": "eu-central-1"
}
}
},
"did": {
"method": "jwk"
}
}
Body Parameters
keybackend: String - Specifies the storage type of key. It can bejwk(manged by you),aws-rest-api(managed by AWS KMS using Rest api requests ) and others. Learn more about different types here.keyType: String - the algorithm used to generate the key. For Vault only ed25519 is possible.configroleName: String - The role name for AWS KMS.region: String - The region where the AWS KMS service is located.
did:method: String - Specifies the DID method. It can be key, jwk, web, cheqd.
Key Usage
Once you have successfully created a key that is one of the supported types listed above, you can use it in sign and issue operations offered by the issuer API.
If you've already had a look at
our /sign, /issue, /batchIssue
endpoints, you have seen that they all follow a similar request body structure, where the key that should be
used for signing credentials is provided via the issuerKey property. Now instead of providing the key as JWK, we
provide
a reference to a key stored in Vault with the required parameters and access credentials.
Below you can see an example of
issuerKey object referencing a key stored in AWS.
{
"issuerKey": {
"type": "aws-rest-api",
"config": {
"auth": {
"roleName": "AccessRole",
"region": "eu-central-1"
}
},
"id": "324ebf67-6bcc-4439-8b81-260bf0a82532",
"_publicKey": "{\"kty\":\"EC\",\"crv\":\"P-256\",\"x\":\"RfvJGDXOjz3NOSKgZ0VlijXST8S-j96DrG0C1AMNAK8\",\"y\":\"vSt2q7yIy0-AhAirMuuDmUScxkgf4JVfId-vTETraQA\"}",
"_keyType": "secp256r1"
},
"issuerDid": "did:jwk:eyJrdHkiOiJFQyIsImNydiI6IlAtMjU2IiwieCI6IlJmdkpHRFhPanozTk9TS2daMFZsaWpYU1Q4Uy1qOTZEckcwQzFBTU5BSzgiLCJ5IjoidlN0MnE3eUl5MC1BaEFpck11dURtVVNjeGtnZjRKVmZJZC12VEVUcmFRQSJ9"
}
Properties
type: String - the type of key can be either "aws" when using AWS KMS or "jwk" when providing the key in full as JWK.id: String - the ID of the key in the Transit Engine.configaccessKeyId: String - The access key id for AWS KMS.secretAccessKey: String - The secret access key for AWS KMS.region: String - The region where the AWS KMS service is located.
_publicKey(optional): Array - The public key can be fetched by the issuer API or directly provided, saving resources and reducing network requests._keyType(optional): String - The key type can be fetched by the issuer API or directly provided, saving resources and reducing network requests. ::
